Click here to go back to the main article "2-D or not 2-D?"
So you've decided to add a QR code to your package to better communicate and/or interact with consumers. Now what? Where do you start? Here's a list of various technologies available to help you find and assess the best one for your project.
QR Code: "QR code" has become the generic term for all types of 2-D codes/tags. These open-source codes are preferred for their high-speed scan capability, ability to hold large amounts of information and relatively small footprint. QR codes can be read with an almost unlimited variety of readers, meaning no specific/proprietary reader is required for a specific QR code. Conversely, not all readers will read all QR codes. QR codes contain the entire message or content within the code. This alleviates the need for online access to decode it. (Source: www.qrcode.com) 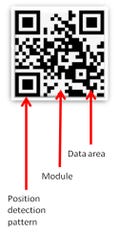
1-TAG: For anti-counterfeiting, Heidelberg's 1-TAG is based on a combination of physical random processes and cryptographic signatures. First, a pattern randomly generated from copper threads is applied to a label. This pattern is read off using a camera, and a cryptographic key that is unique to each manufacturer converts it into an equally unique code. This cryptographic signature ensures that the random pattern, code and product information are linked up in such a way that they offer reliable protection against manipulation. The code is printed on the label next to the pattern of copper threads using a digital drop-on-demand inkjet system. To check the authenticity of a product labeled with 1-TAG technology, end customers only need their smartphone and the free 1-TAG app. The software scans the security label and detects immediately whether the content of the QR code matches the pattern of the neighboring copper threads or not. This process does not require access to the mobile data network, which means that the check is free of charge across the globe. In addition to the result of the check, the app also displays the corresponding brand, the product name, and the size of the packaging and can supply end customers with additional product-specific information. (Source: Heidelberg, www.heidelberg.com) 
Any package graphic: The Aurasma smartphone app merges our physical and virtual worlds. With this technology, consumers use their cellphones, but there's no "code" per se. Any graphic will do. Using the smartphone's camera, GPS, compass, accelerometer and internet connection, the technology combines image recognition and a conceptual understanding of the 3D world to recognize objects and images and seamlessly merge augmented reality actions into the scene. Without the need for bar codes or tags, the app is able to see its surrounding environment and make it fully interactive. Source: Aurasma, www.aurasma.com)

Aztec
Aztec: The Aztec code is a two-dimensional matrix-type 2-D code. It consists of dark and light square data modules. Aztec codes use a finder pattern of concentric square rings centered on a single dark module located in the center of the code. (Source: AIM, www.aimglobal.org)
Data Matrix
Datamatrix: Data matrix codes consist of dark and light square data modules. They have finder patterns of two solid lines and two alternating dark and light lines on the perimeter of the symbol. A 2-D imaging device, such as a CCD camera, is necessary to scan the code. Data matrix is used for small item marking applications. (Source: AIM, www.aimglobal.org)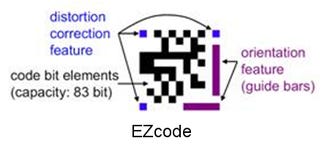
EZcode
EZcode: EZcode 2-D bar code symbology was created specifically for the mobile camera phone in 2005. It has a simple, yet effective design which allows it to be read at a smaller size (0.5-in.), by a higher number of mobile devices. An EZcode can remain the same size no matter how much information you put into it. Using the ScanLife platform, you can create your codes, edit the content at any time and see updated performance analytics. (Source: ScanBuy, www.scanbuy.com)
Grid Matrix
Grid Matrix: The Grid Matrix code is a variable-size, 2-D matrix code. It consists of dark and light framed "macro modules" that create a grid design that provides a robust finder pattern. The unique finder pattern ensures readers can locate and orient the symbol even with significant symbol damage. (Source: AIM, www.aimglobal.org)
Han Xin code
Han Xin: Developed by the Assn. for Automatic Identification and Mobility (AIM) Technical Symbology Committee (TSC), the Han Xin data matrix code is a variable size symbology, specifically optimized for two- and four-byte alphabets such as Chinese and other ideographic and pictographic alphabets. Among the 84 size and symbol versions are options for encoding graphics and audio, making it suitable for mobile marketing and consumer packaging applications. (Source: AIM, www.aimglobal.org)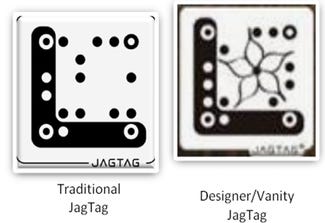
JagTag
JagTag: Recently redesigned and renamed "QR code-powered JagTag," this code can be "branded" with logos and graphics. Although JagTags are a closed, proprietary platform, they do not need a proprietary reader or a "smart"phone. They work via picture text messaging (Multimedia Messaging Service/MMS) and can be accessed by smartphones or standard "feature" phones with a text plan. Response time for JagTag content varies: It can be as fast as a few seconds to as slow as several minutes or hours. JagTags do not require an Internet connection but can be linked to mobile or static URLs, if necessary. (Source: Augme, www.augme.com)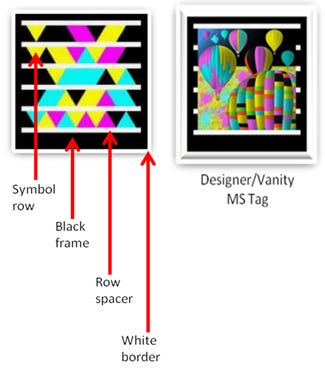
MS tags
MS Tag: Because Microsoft Tags (MS Tags) are a "closed" platform and require a proprietary MS Tag reader, Microsoft supports analytics/reporting. MS Tags are generally more "secure" than QR codes, in part because content is stored on Microsoft servers, which gives Microsoft the ability to block certain URLs, as well as require an optional opt-in password. While MS Tags work particularly well in low-light situations, they do not work well on curved or rounded surfaces, or from an angle. The vector-format tags can scale in size without compromising readability. They can be produced and scanned in either color or black and white, and in standard or designer/vanity versions. The symbols within a standard MS Tag are triangles. For designer/vanity MS Tags, the symbols can be dots. (Source: Microsoft, www.tag.microsoft.com)Near Field Communication: Based on existing radio-frequency identification (RFID) technology, near field communication lets a smartphone "talk" to an NFC chip embedded in a package simply by bringing the phone close to the tag. ComputerWeek.com gives a non-packaging example of how this contactless technology could be used (but you'll get the idea of how it would work with packaging): "Embedding an NFC chip in a movie poster where, when you touch the phone to the poster, a trailer of the film appears on YouTube on your phone."
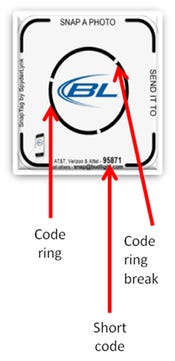
SnapTag
SnapTag: SnapTags are read by the "code rings" (the three breaks in the ring), which can be moved to an almost infinite combination of positions, with each position creating a new code with unique content. SnapTag can either be read with SnapTag's proprietary reader app, or a picture of the tag can be "snapped" and then texted via a short code (an abbreviated 5 or 6-digit phone number) or emailed. Users must opt in to all short code content before it is delivered. (Source: Spyderlynk, www.spyderlynk.com)About the Author(s)
You May Also Like




