Increasing security in the supply chain with RFID tags
February 4, 2014
There's a new twist on using radio frequency identification (RFID): Smart electronic security markers, based on RFID technology. These markers are making an impact with item-level security and are laying the groundwork for this kind of protection in future applications. RFID tags embedded at the product-item level make it easier to guarantee authenticity and represent an increasingly important value proposition for RFID by protecting product and brand integrity.
This paper will take a look at the size and most common means of counterfeiting today in the pharmaceutical and consumer products industry as well as with peripheral or replacement market products. It will also propose a range of increasingly secure methods of using RFID to prevent some of the different types of counterfeiting.
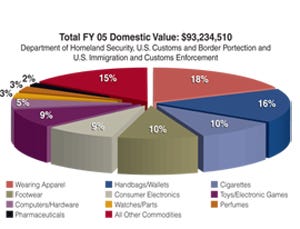
Figure 1. The chart above shows counterfeit products that were seized in 2005 by U.S. Customs and Border Patrol. The products are segmented according to type.
Counterfeiting continues to grow and has become a worldwide problem that has reached “epidemic proportions,” according to DNA Technologies (www.dnatechnologies.com) [a security company employing DNA-based tracking technology to combat counterfeiting, piracy and product diversion] in its report entitled, “The 21st Century Solution to Counterfeiting, Forgery & Diversion”(1). DNA Technologies estimates that while eliminating more than 750,000 jobs, counterfeiting costs American businesses more than $200 billion in revenues every year. This doesn't take into account activity in other areas of the world that can reach 5 to 8 percent of the total world trade. One of the problems in addressing counterfeiting is that it can take different forms in the supply chain at the item level or through diversion. The most prolific abuse is the counterfeited product at the item level, for example, brand-name apparel, electronics and pharmaceutical products (See Figure 1).
Counterfeit and compromised drugs have been increasingly making their way into the public healthcare system and have been identified as a threat to the public health by the U.S. Food and Drug Administration. In 2004, the FDA reported 58 counterfeit drug case—a tenfold increase since 2000 (3). In China, it's estimated that in one year, 192,000 Chinese patients died from “fake” drugs. In Nigeria, nearly 2,500 people were killed through injecting a supposed anti-meningitis drug during an international vaccination campaign.
Another example of item-level counterfeiting is with peripheral electronics equipment, such as replaceable ink-printer cartridges. Since a manufacturer usually earns the highest margin for a system from the peripherals or replacement goods, counterfeit peripherals impact the manufacturer's profitability. They can also cause problems with the quality and operational performance of the system.
Diversion is the use of an unauthorized channel in the supply chain and is another form of counterfeiting. Branded cosmetics sold at flea markets by unauthorized vendors or pharmaceutical products purchased at a senior citizen discount to unqualified individuals are examples of diversion. Diversion typically occurs because of differentiated price structures within an intended channel or between market segments with different qualifications. Channel corruption in the supply chain can distort profits and revenue distribution, which can lead to additional black-market activities as well as diminished brand value.
The current anticounterfeiting methods are usually classified as either overt or covert packaging technologies. Overt technologies on packages are visible to the eye and include methods such as optical, variable inks in which colors shift as the user moves the package between various viewing angles. There are tamper-evident techniques that indicate package manipulation such as plastic [shrink film or a shrink band] covering the cap on medicine bottles.
Covert technologies are integrated into packaging and are invisible to the naked eye. They include such methods as ultraviolet/infrared light elements that can only be detected with special equipment or microscopic/nanotextimages and complex printing that's difficult to replicate.
Whether overt or covert methods are utilized, the need for human involvement remains an overriding requirement for their use. In many supply-chain scenarios, everyone in the supply chain—from receiving clerks to stockers to checkout clerks—is required to be aware of the overt method used. Due to the complexity and the number of touchpoints in the system, this often leads to anticounterfeit tactics that are ignored, compromised or not utilized in a way that makes them fully effective. Therefore, covert and overt approaches are often used after there is already a suspicion that a problem exists.
RFID technology provides ways to prevent illegitimate products, peripherals and channels from [continuing to move through the supply chain].
A typical RFID system comprises three main elements, which include an RFID tag, a reader and a host processor. The system uses a microchip in the transponder (tag) to store and transmit data via radio signals. Through the transponder's antenna, the tag receives an electromagnetic signal at the appropriate frequency from an RFID reader. The passive tag (meaning it has no battery) is charged with enough energy to communicate with the RFID reader and provide the reader with data stored on the tag.
RFID protects products by removing the propensity for counterfeiting through human involvement by providing an embedded, electronic security marker that's automatically read as it passes through the supply chain either individually or as a group inside a shipping case. An electronic security marker is a unique data code that, by itself or in conjunction with a network, can distinguish the product as genuine. This marker is unique to the individual product and cannot be easily altered, providing an enhanced level of security. Combined, the attributes of being both automated and highly secure give an electronic security marker many advantages over traditional covert and overt marking techniques.
In peripherals, if the security marker on a tag is deemed legitimate by the host processor, then the product is accepted in the application. As the product travels through the supply chain, the electronic marker is picked up by RFID readers that authenticate the products as genuine. The authentication happens either directly between the reader and tag, or by retransmitting the data to a network and validating the information.
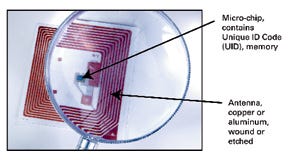
Figure 2. The micro-chip and antenna, above, are significant elemnts of an RFID transponder (tag).
Authentication of the tag data can be either on- or off-network. As an example of an on-network solution, EPCglobal Inc. (www.epcglobalinc.org) is creating an Electronic Product Code (EPC) item-level serialization scheme for item-level tags. They will serve as electronic security markers unique to each product. The vision is for products to have automated track-and-trace capabilities, as well as real-time visibility of the product through the EPCglobal Object Name Service (ONS) Network. The EPCglobal ONS will act as a traffic cop and direct authorized network inquiries to the proper database hosting the desired data.
The off-network method enables RFID readers to authenticate the tag through a shared-data encryption algorithm. An electronic security marker can be a digital signature generated via a public-key infrastructure (PKI) and programmed into the tag's memory.
A reader may validate the tagged product because the reader is supplied with the appropriate manufacturer public key to authenticate the digital signature. PKI relies on public-key cryptography, which uses a pair of mathematically related cryptographic keys—a public key and a corresponding, unique private key.
While the keys are mathematically related to each other, given proper key length, it's computationally infeasible to calculate one key's encryption from the other. When using an RSA encryption, [a method of dual key (public key) encryption, based on the public key system, meaning that every user has two digital keys—one to encrypt information; the other to decrypt] a 1,024-bit-size digital signature will prohibit a brute force attack to gain knowledge of the cryptographic private key (4).
By using a digital signature, a manufacturer's unique, “electronic fingerprint” is created and is programmed into the tag, which can then be authenticated by a reader without a network.
Already, examples of RFID item-level tagging today are designed to protect product integrity. These cross various industries and address the problems of illegitimate products and channels.
RFID electronic security markers are also used in many medical-equipment systems, such as ventilators, to ensure that authentic peripheral products are used with the host system. Typically, RFID reader chip sets are built into medical equipment and are used to read tagged peripheral products as they're connected. The benefit is first and foremost patient safety. Having the correct peripheral with the appropriate medical equipment ensures the parts will operate together as they were designed, which can be a matter of life or death. Additional benefits include product authentication, automated calibration and setup information in various medical equipment that's RFID-enabled.
Patient safety is the key force behind pharmaceutical item-level tagging. RFID enables track-and-trace through the EPCglobal ONS networks and/or direct authentication with off-network RFID readers. As more products are tagged, supply-chain efficiencies will occur at the manufacturer, wholesaler and pharmacy. Markers protect and manage clothing at retail stores such as British retailer Marks & Spencer, which plans to tag clothing at the item level in six departments at 53 stores this year (5).
Tagging high-end clothing also helps to prevent diversion in the supply chain. With item-level tagging, if a legitimate item is diverted, it can be verified with a security marker and traced back to the point of diversion.
Electronic products can be enabled with RFID security markers to protect peripheral authenticity. Many electronic systems rely on peripheral products to perform as intended. And too often, electronic retailers are stuck with counterfeit or damaged goods when they are returned to stores by dishonest patrons. Electronic security markers can tie the relationship of a particular product to a given sale and to the return.
Manufacturers could benefit from the elimination of fraudulent products being returned to retailers by placing item-level RFID tags on their high-end products and components.
RFID tags on beauty product containers can protect that sales channel, which is an integral element to the success of the business model. For example, it's important that high-profile cosmetic brands sold through direct sales are not undermined by some of the product being diverted and offered by street vendors.
RFID tags embedded into packaging can be used to identify diverted product being offered through street vendors. Also, electronic security markers indicate the product pedigree, pointing to where the improper channel diversion occurred.
Protecting product and brand integrity is a challenge, and counterfeiting continues to grow. But it's already becoming a new value proposition for RFID. Controlling product legitimacy in the supply chain may become a nonissue for manufacturers some day, as the use of electronic security markers will curb counterfeiting at item/product levels.
References: |
|
Joseph Pearson, the author of this and other white papers, is a business development manager at Texas Instruments' Radio Frequency Identification (TI-RFid™) Systems. For more information, visit TI's website at www.ti.com/rfid. |
You May Also Like


